If your go-to LinkedIn Chrome extension suddenly stopped working, you’re not alone. The simple answer is that LinkedIn actively detects and blocks tools that violate its policies on automation and data scraping. This isn't a glitch; it's a deliberate defense mechanism designed to protect user privacy, prevent spam, and maintain the integrity of its professional network.
The Real Reason Your LinkedIn Extension is Blocked

For busy sales teams, recruiters, and marketers, a non-functional extension can disrupt your entire workflow. One day you’re efficiently building lead lists or sourcing candidates, and the next, your most valuable tool is rendered useless. Understanding why this happens is the first step toward finding a smarter, more reliable solution for your lead generation needs.
The core of the problem is a fundamental conflict: many Chrome extensions are built to perform actions that are explicitly forbidden by LinkedIn's User Agreement. Most tools that automate profile interactions or scrape data operate in a gray area that LinkedIn considers a direct violation of its terms.
The Cat-and-Mouse Game of Detection
LinkedIn is constantly updating its platform to detect and shut down these unauthorized tools. This has created a relentless "cat-and-mouse" game where extension developers find a temporary workaround, LinkedIn patches the vulnerability, and you—the professional relying on the tool—are left with a broken workflow.
LinkedIn’s motivations are straightforward and business-focused:
- Protect User Data: Preventing unauthorized third-party apps from harvesting member information is a top priority.
- Maintain Platform Quality: The goal is to eliminate spammy, robotic behavior that degrades the user experience.
- Control the Ecosystem: LinkedIn wants users to engage with the platform (and its paid features, like Sales Navigator) as intended.
The consequences are real. In the last year, LinkedIn has shut down several major automation extensions, restricted thousands of user accounts, and pursued legal action against tool creators.
The message is clear: LinkedIn is the gatekeeper of its platform, and it will penalize both the tools and the users who violate its rules. Using a non-compliant extension puts your professional account at significant risk.
This creates a major challenge for professionals who depend on efficient data collection for their roles. When your primary lead generation tool fails, productivity grinds to a halt. If you're currently dealing with this, understanding why your LinkedIn scraper is not working can provide immediate clarity.
The solution isn't to abandon efficiency—it's to adopt safer, smarter tools. Instead of relying on extensions that send a flurry of automated requests on the site, modern alternatives like ProfileSpider have adopted a local-first, one-click approach. By extracting profile information on your machine without behaving like a bot, these tools drastically lower the risk of detection and help safeguard your account.
Let's break down the main reasons your extension might be blocked. The following table summarizes the key factors, from LinkedIn's official policies to the technical triggers they use for enforcement.
| Reason for Block | What It Means for You | LinkedIn's Motivation |
|---|---|---|
| Policy Violations | The extension performs actions (like automated scraping) that violate LinkedIn's User Agreement. | Protecting user data, preventing spam, and ensuring platform integrity. |
| Technical Detection | The extension triggers LinkedIn's bot-detection systems through robotic, high-volume, or unusual activity. | Differentiating human users from automated scripts to maintain a high-quality user experience. |
| Rate Limiting | Your account exceeds the maximum number of actions (e.g., profile views, connection requests) allowed in a specific timeframe. | Preventing server overload and curbing aggressive, spam-like behavior from a single account. |
| Browser/Store Issues | The extension violates Chrome Web Store policies (e.g., outdated Manifest V3 compliance) or has security flaws. | Ensuring extensions are secure, performant, and don't create a bad experience for Chrome users. |
Understanding these factors is essential for any professional who wants to avoid account suspension while still achieving their lead generation and recruiting goals.
Decoding LinkedIn's Rules on Automation and Scraping
To understand why so many Chrome extensions fail on LinkedIn, you must first understand the platform's rules. Buried within LinkedIn’s Terms of Service are specific clauses that directly prohibit the core functions of most automation and scraping extensions.
For sales professionals, recruiters, and marketers, translating this legal language into practical, safe workflows is key to protecting your account. LinkedIn isn’t trying to make your job harder; it's focused on protecting its members and their data.
The Core Prohibitions Explained for Business Users
LinkedIn’s User Agreement is unambiguous when it comes to third-party software. The platform explicitly forbids any tool that automates actions or scrapes data without its direct, written consent. This isn’t a gray area—it's a firm rule designed to maintain the platform's professional environment.
LinkedIn's enforcement focuses on three main activities:
- Unauthorized Software: This includes any browser extension, bot, or script that interacts with LinkedIn’s interface on your behalf. If it's not an official partner application, it's technically against the rules.
- Automated Actions: Tools that auto-connect with hundreds of profiles, send templated messages in bulk, or automatically view profiles are the primary targets. This behavior mimics spam and degrades the user experience.
- Data Scraping: Using software to systematically extract profile data—names, job titles, emails, company info—is strictly prohibited. LinkedIn views this as a violation of both user privacy and its own intellectual property.
These rules exist to prevent the platform from being overrun by spam, fake engagement, and unethical data harvesting operations that exploit its members.
Where Policy Meets Everyday Workflows
So, how does this impact your daily tasks? Many common extension features, which seem like simple productivity boosters to recruiters and sales teams, are clear violations in LinkedIn's view.
A salesperson using an extension to send 200 connection requests per day is engaging in prohibited automation. A recruiter using a tool to scrape a list of 500 potential candidates from a search result is performing forbidden data scraping. To better understand the platform's perspective, it helps to be familiar with the broader concept of content automation, which provides context for these platform-specific rules.
LinkedIn's enforcement is programmatic, not personal. Its algorithms are trained to detect patterns of behavior that indicate rule-breaking, which can trigger automated warnings, restrictions, or even permanent account bans.
Understanding the Legal and Ethical Boundaries
The debate over data scraping extends beyond LinkedIn's policies, touching on significant legal and ethical considerations, especially regarding personal data. For a comprehensive overview, our guide on whether website scraping is legal explores this complex landscape.
Ultimately, using a non-compliant tool puts your account—and potentially your company's reputation—at risk. The convenience offered by a risky extension is often short-lived, ending as soon as LinkedIn’s detection systems adapt. This is precisely why a new generation of privacy-first, no-code tools operates differently.
For example, a modern tool like ProfileSpider uses a local-first processing model. Instead of automating actions on the platform and triggering alarms, it simply extracts the data you can already see, directly on your own machine. This one-click workflow respects platform boundaries because it doesn't behave like a bot, significantly reducing the risk of detection. It's a smarter, safer way to build lead lists without violating terms of service.
How LinkedIn Technically Detects and Blocks Extensions
Ever wondered why your favorite Chrome extension suddenly stopped working on LinkedIn? It’s not a random event. You've encountered LinkedIn's sophisticated digital immune system, which is designed to detect and disable tools that violate its rules. This system is constantly evolving and getting smarter.
For recruiters, sales teams, and marketers who rely on these tools for lead generation, understanding these technical defenses is crucial. It explains why so many extensions eventually fail and why choosing a tool built for safety—not just speed—is essential.
Spotting the Digital Footprints of Automation
At its core, LinkedIn’s defense mechanism is about distinguishing between human and bot activity. Most automation tools, particularly older or poorly designed ones, leave obvious digital footprints that are easily identified by LinkedIn's algorithms. They perform actions with a speed and consistency that no human can replicate.
Imagine a recruiter manually clicking the "Connect" button on 20 profiles. Each click is slightly different. The timing varies, the mouse path is unique, and the cursor never lands on the exact same pixel twice.
Now, consider an extension performing the same task. It might click the exact same pixel, in the exact same way, every 500 milliseconds. This robotic, unnatural precision is a major red flag for LinkedIn’s bot detection systems.
Browser Fingerprinting: The Unseen Identifier
One of LinkedIn’s most effective weapons is browser fingerprinting. This technology allows the platform to create a unique digital signature of your browser, including the extensions you have installed. It’s like a digital detective identifying unique characteristics at a crime scene.
LinkedIn's sophisticated browser fingerprinting can identify extension signatures, detect automation scripts like Puppeteer or Selenium, and flag unnatural behavior such as overly precise or rapid clicking. Once an account is flagged, it can face shadow restrictions, temporary lockouts, or even a permanent ban. This is a significant risk, as most extensions mimic human actions without LinkedIn's permission, placing user accounts in jeopardy.
This means LinkedIn can often detect:
- Extension Signatures: The specific digital traces left by known automation extensions.
- Headless Browsers: Clear evidence that a script (like Selenium or Puppeteer) is controlling the browser, not a person.
- Behavioral Anomalies: Any activity patterns that do not appear human.
These digital identifiers make it extremely difficult for most extensions to remain undetected. If you've ever had other tools like the Apollo extension stop working, you've witnessed a platform's defense mechanisms in action. We explore this further in our guide on common issues with the Apollo extension on LinkedIn.
This diagram illustrates how LinkedIn's core rules directly inform the technical enforcement against automation, scraping, and unauthorized software.
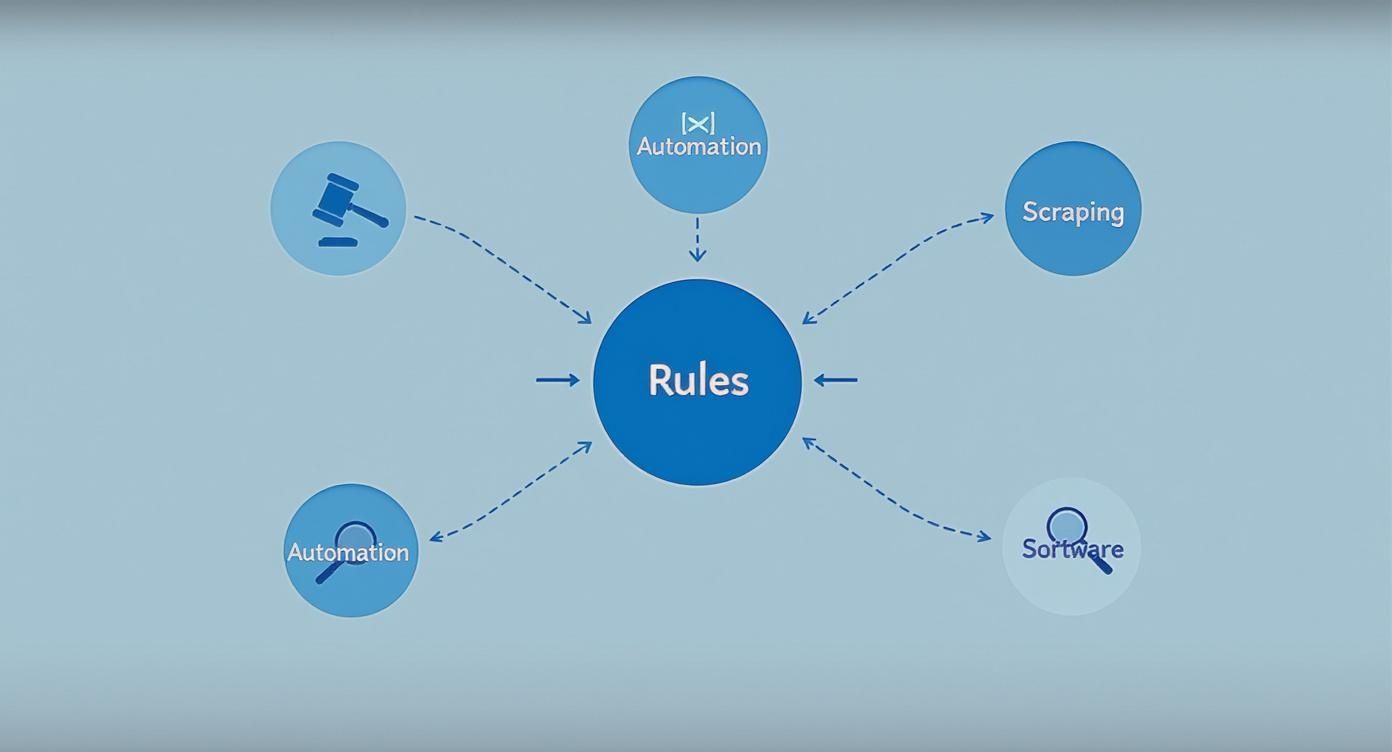
The key takeaway for professionals is that LinkedIn's technical defenses are not random; they are a direct extension of its platform policies, creating a robust system to block non-compliant tools.
Rate Limiting and Network-Level Defenses
Another critical defense is rate limiting—an invisible speed limit on your account. LinkedIn has internal limits on how many profiles you can view, connection requests you can send, or searches you can perform within a specific timeframe.
When an extension exceeds these limits—for example, by attempting to view 1,000 profiles in an hour—it triggers an immediate alarm. This is one of the most common ways accounts get flagged for suspicious activity, often resulting in a temporary restriction or a formal warning.
LinkedIn also monitors for suspicious patterns at the network level. If it detects a flood of automated requests from a single IP address or source, it can block them entirely, effectively cutting the extension off from its servers.
This is precisely why a tool like ProfileSpider was designed with a fundamentally different, no-code approach. By running locally on your machine and focusing on one-click extractions instead of continuous automation, it avoids many of these technical triggers. It doesn't behave like a bot, helping to ensure your account activity appears natural and human.
Browser and Web Store Policies That Cause Blocks
It's not always LinkedIn's fault. Sometimes, the block originates from the gatekeeper of extensions: the Chrome Web Store. Google has its own strict set of rules, and any extension that violates them is quickly disabled or removed. This can have a ripple effect that inadvertently gets your LinkedIn account flagged.
For anyone in sales, recruiting, or marketing, this adds another layer of complexity. You're not just trying to comply with LinkedIn's policies; you also have to ensure your tools meet Google's ever-tightening standards for security and performance. If Google doesn't trust an extension, you can be sure LinkedIn won't either.
The Manifest V3 Challenge
One of the most significant technical challenges for extension developers has been Google's transition to Manifest V3 (MV3). A "manifest" is the blueprint for an extension, dictating to Chrome what it's allowed to do. MV3 is the new, much stricter blueprint designed to make extensions safer, more private, and more performant.
However, this enhanced security came at a cost for many data scraping and automation tools. MV3 severely restricted an extension's ability to run scripts in the background—a core function for any tool that continuously scrapes data or automates actions. This single change rendered many older, more aggressive LinkedIn extensions obsolete.
By mid-2025, all extensions must comply with MV3, or they will be blocked from the Chrome Web Store. Many LinkedIn automation tools were caught in this transition because their entire functionality was built on features that MV3 now restricts or forbids. For more context, AboutChromebooks.com has a great piece on commonly blocked extensions.
The Problem of Overly-Permissive Extensions
Another major red flag for both Google and LinkedIn is an extension that requests excessive permissions. When you install an extension, it asks for your consent to perform certain actions. A trustworthy tool will only request the absolute minimum permissions needed to function.
However, less reputable extensions often demand dangerously broad access, such as:
- "Read and change all your data on all websites": This is the most dangerous permission, effectively giving the extension full access to your entire online activity—including your banking, email, and LinkedIn account.
- "Access your browsing history": This allows the extension to track every site you visit, creating a detailed and invasive profile of your online behavior.
- "Manage your downloads": While sometimes legitimate, this permission can be abused to download malicious files to your computer without your knowledge.
If an extension requests permissions that seem unrelated to its stated purpose, it's a clear warning sign that it may be harvesting your data. LinkedIn's security systems are designed to be wary of accounts using extensions with such invasive access.
This is why modern, privacy-first tools are built differently. A tool like ProfileSpider, for instance, operates on a local-first philosophy. This means all the data it extracts is stored directly in your browser, not on a third-party server. It doesn’t need invasive, all-access permissions because its function is simple and transparent: extract the profile information you're currently viewing and save it locally for you to export. This approach aligns with the security-focused direction of both Chrome and LinkedIn and dramatically reduces the risk of your account being flagged for using an unsafe tool.
Understanding the Data Privacy and Security Risks
Beyond the immediate threat of an account suspension, the most significant reason LinkedIn cracks down on extensions is data security. For a platform built on professional trust, user privacy is a fundamental promise. Any tool's approach to data is a critical factor in LinkedIn's enforcement strategy.
When you install a Chrome extension, you are granting a third-party developer access to your professional network and data. Many users click "accept" on permission requests without fully understanding the implications.
The consequences can be severe. Some extensions are designed to scrape Personally Identifiable Information (PII) without consent. They don't just access your data; they often collect your contacts' information and transfer it to unknown third-party servers, creating a major security vulnerability.
The Hidden Dangers of Data Harvesting
Using an insecure extension doesn't just put your LinkedIn account at risk; it can expose your entire company to serious legal and reputational damage. If that tool mishandles data, you could inadvertently violate strict privacy laws like GDPR or CCPA, leading to substantial fines and a loss of client trust.
This brings in broader business concepts like third-party risk management. Every extension you install is a new vendor, and without proper vetting, you introduce an unmanaged risk into your operations.
The scope of this problem is significant. A recent analysis of AI-powered Chrome extensions revealed that 67% collect user data and 41% gather PII. As you can discover more insights about these privacy risks, it becomes clear why platforms like LinkedIn are so aggressive in blocking tools that are careless with user information.
Choosing a Privacy-First Approach for Lead Generation
This intense focus on data security highlights the value of choosing modern, privacy-first tools—those designed to respect both platform rules and user confidentiality. The critical difference comes down to one question: where is your data processed and stored?
Many high-risk extensions are cloud-based. They scrape your data, send it to their own servers for processing, and store it remotely. This model introduces several points of failure:
- Data Interception: Your information is vulnerable as it travels from your browser to their server.
- Server Security: You have no control over how well their servers are protected from breaches.
- Data Misuse: The company could potentially sell or misuse the data belonging to you and your contacts.
In contrast, a "local-first" approach keeps all your sensitive information securely on your own machine. It never leaves your control, completely eliminating the risks associated with third-party servers.
This is the exact model ProfileSpider is built on. It operates entirely within your browser, analyzing profile data locally without ever sending it to an external cloud. All the information you extract stays on your computer, ensuring your data—and your clients' data—remains secure and confidential. This design not only protects you from data breaches but also helps you stay compliant with privacy regulations, making it a fundamentally safer choice for lead generation and recruiting.
Adopting Safer Practices for LinkedIn Lead Generation

After examining LinkedIn's policies and technical defenses, the path forward for professionals becomes clear. You don't have to abandon your lead generation or recruiting goals—you simply need to adopt a smarter, safer workflow. This involves shifting away from aggressive, high-volume automation and embracing a "human-first" approach.
Instead of trying to automate hundreds of interactions a day, the goal should be to build highly targeted lists and engage with prospects authentically. This strategy respects both the user and the platform’s rules.
Embrace Local-First Data Processing
A critical component of a safer strategy is changing how and where your data is processed. The riskiest extensions are cloud-based, scraping data and sending it to their own servers. This creates both major privacy issues and leaves an obvious digital trail for LinkedIn's detection systems to follow.
The modern, safer alternative is local-first data processing. With this model, all the profile information you gather is extracted and stored directly on your own machine. It never touches a third-party server.
By keeping the entire process contained within your browser, you minimize the technical signals that trigger LinkedIn's alarms. Local-first tools aren't automating actions on the platform or sending suspicious network traffic, making them fundamentally less risky.
This is the core principle behind no-code tools like ProfileSpider. It analyzes the webpage you're currently viewing and lets you extract visible profile data with a single click. The information is processed and saved locally, giving you complete control and privacy while dramatically lowering the risk of your account being flagged. It’s a powerful way to build lead lists without acting like a bot.
Your Checklist for Evaluating Tool Safety
Before installing any third-party tool for LinkedIn, think like a security analyst. Understanding why Chrome extensions get blocked on LinkedIn is the first step to making smarter choices. Use this checklist to evaluate the risk level of any tool before you click "Add to Chrome."
For a deeper dive into this topic, you can also review these essential lead generation best practices.
Here's a quick rundown of what to look for when vetting a tool.
Checklist for Evaluating LinkedIn Tool Safety
| Safety Check | What to Look For (Green Flag) | What to Avoid (Red Flag) |
|---|---|---|
| Data Handling | Processes and stores data locally on your computer. Explicitly states a "no cloud storage" or "local-first" policy. | Sends your data to a third-party server for processing or storage. Vague privacy policy. |
| Automation Level | Focuses on one-click data extraction or enhances the UI without automating actions like messaging or connecting. | Automates connection requests, messaging, profile views, or endorsements in high volumes. |
| Permissions | Asks for minimal permissions required for its core function (e.g., "access data on the active tab"). | Demands broad, invasive permissions like "read and change all data on all websites." |
| User Reviews | Recent reviews are positive and mention account safety, reliability, and good customer support. | Multiple recent reviews mention account restrictions, bans, or the tool suddenly stopped working. |
Ultimately, choosing the right tool comes down to prioritizing your account's long-term health. Green flags indicate tools designed with respect for platform rules, while red flags often point to shortcuts that could lead to account suspension.
Frequent Questions About Blocked LinkedIn Extensions? We’ve Got Answers.
It’s a frustrating experience—one moment you’re efficiently working with a helpful extension, and the next, LinkedIn has restricted your account. It's confusing and can bring your sales or recruiting workflow to a screeching halt.
Let’s address the most common questions professionals have when this happens, so you can understand what went wrong and how to proceed safely.
How Do I Know If My LinkedIn Account Is Restricted?
You’ll typically notice a few clear signs. Connection requests may fail to send, or your messages might get stuck without being delivered. In some cases, your search results may seem unusually limited, or you might receive an official warning notification directly from LinkedIn.
If you suspect a restriction, your first step should be to disable all of your LinkedIn-related extensions immediately.
If the issues persist after disabling your tools, your account is likely under a temporary restriction. The best course of action is often the most difficult: reduce your activity. Keep your interactions to a minimum for a few days. Contacting support can sometimes draw more unwanted attention, whereas allowing the restriction to lift on its own is often the safest path.
Are All LinkedIn Chrome Extensions Risky?
Not all extensions are created equal, but you must be discerning. Any tool that automates actions on the platform—such as auto-sending connection requests or messages—is high-risk. The same applies to extensions that scrape data by communicating with a cloud server; that network activity is a significant red flag for LinkedIn.
The safest tools are those that either enhance the user interface without automation or extract data locally on your computer. Before installing any tool, always check its permissions and read recent user reviews—they often reveal everything you need to know about its safety and reliability.
So, What's the Safest Way to Gather Leads on LinkedIn Now?
The landscape has shifted. The most reliable and sustainable strategy is a combination of targeted, manual outreach and the use of privacy-first tools that operate locally. This approach helps you avoid triggering the alarms that high-volume, aggressive automation inevitably sets off.
Instead of relying on cloud platforms that operate from remote servers, consider a no-code tool like ProfileSpider that runs entirely on your machine. This one-click workflow allows you to export the profile data you need for your CRM without leaving the digital footprints that lead to account restrictions.
Ultimately, it comes down to this: prioritize quality interactions over sheer quantity. Stay within a reasonable daily activity limit, choose your tools wisely, and you’ll keep your account in good standing for the long term.